Think Security Breaches Are the Biggest Threat to Your Company? Think Again.
In 2018, IT was thrust squarely in the spotlight, and not in a good way. Over 1 billion people had their personal data exposed thanks to security breaches. Facebook, T-Mobile, Quora, Google, Orbitz, and dozens of other companies all had sensitive customer data compromised. Aside from the immediate financial impact of a breach (which averages around $3.86 million per incident ), a damaged reputation and loss of customer trust can cost companies’ millions more in lost business over time.
When breaches happen, the boardroom’s blame is often focused on IT leadership. After the 2013 hack of Target stores, the company faced intense criticism over their data handling practices, culminating in the resignation of their CIO the next year. With so much at stake, it’s no wonder security and governance remain the top areas of focus for IT.
But while they make headlines, security breaches are not the only threat to the enterprise. There’s another more subtle danger that may have an equal impact and longer-lasting consequences — overly rigid governance that inhibits creativity and innovation.
Security vs. Innovation
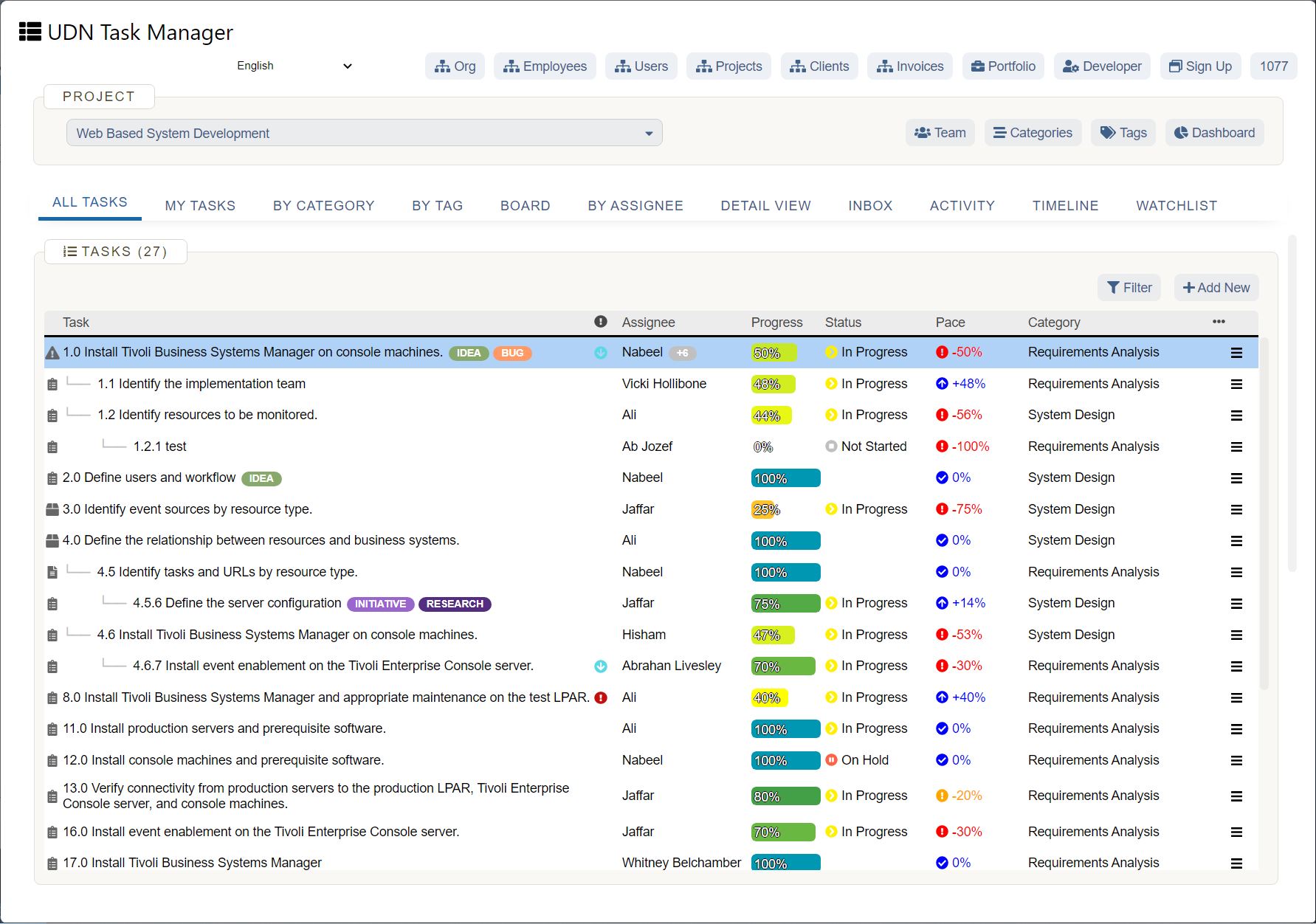
Companies have to be forward thinking and select solutions that they can build on for years or decades to come, while at the same time keeping pace with a rapidly changing market. IT leadership is struggling to find a balance between keeping their organizations safe while remaining flexible enough to enable rapid innovation.
According to the Harvey Nash/KPMG CIO Survey 2018 , “improving cybersecurity” had the greatest increase in priority of all other business areas, jumping up 23%. With the ever-present threat of a security breach hanging over their heads, IT leaders have been quick to lock down every risk point. Compared to marketing leaders, who are eager to leverage new technology to solve their problems, IT leadership can often be seen as killjoys and inhibitors of innovation.
In a piece for Inc. , contributing editor Geoffrey James argued that impeding progress was par for the course for most CIOs:
“In the 1970s, CIOs clung to clunky IBM mainframes when minicomputers and workstations were cheaper and had better software.
In the 1980s, CIOs clung to centralized computing and character cell terminals rather than embrace the PCs and Macs that people actually wanted to use.
In the 1990s, CIOs clung to tightly integrated client-server applications and generally fought against cloud-based applications (like Salesforce.com) that ran across the Internet.
In the 2000s, CIOs clung to overly complicated ERP systems and PCs while their users were rapidly embracing smartphone and tablets.”
But at the same, boards have tasked CIOs and the IT org with promoting innovation, creativity, and experimentation. It’s a tightrope walk, made even more complicated by other departments and even C-level partners adopting new technologies outside of IT. So what can IT leaders do to fulfill their obligations while pushing their organizations forward?
From Technology Managers to Drivers of Business Innovation
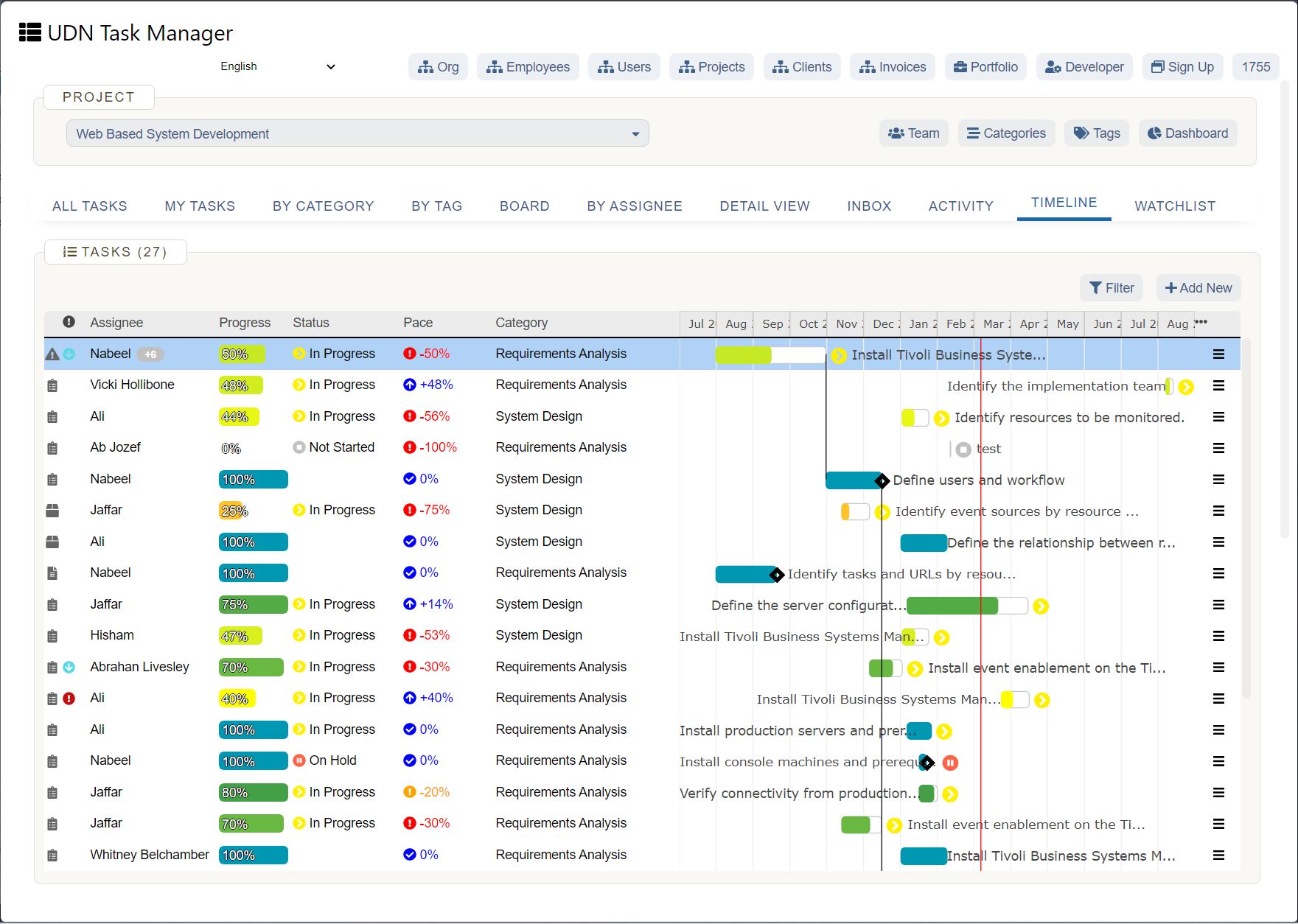
Gone are the days when company leaders would set strategy, and it was IT’s job to implement. Choosing the wrong technology, integration, or partner can result in consequences that could affect the business for years. A radical shift has occurred, with IT and Security leaders taking on a much more advisory role.
“Beginning in the late 1990s, and more so in the last 10 years, Security and IT leadership has been moving to the forefront of corporate decision making,” says Lucas Szymanowski, Director of Information Security at UDN Task Manager . “As organizational security and compliance programs mature, the security organization is seen as a decisive voice involved in choosing partners, vendors, and defining technology landscapes.”
IT leaders have the opportunity to not just maintain and protect company data and technical infrastructure, but also help organizations make critical decisions and investments in technology that can impact overall competitive strategy. Instead of just being responsible for the creation of the technical systems companies rely on, IT leaders are increasingly accountable for the business outcomes those systems can help deliver.
It’s an exciting time, and a huge opportunity for IT to build influence, increase their value, and establish themselves as strategic business partners.
In the Harvey Nash/KPMG CIO Survey 2018 , Bridget Gray, MD, Harvey Nash Australia, highlighted the opportunity this way:
To make this transformation a success, IT leaders need to have an unbiased, business-focused approach to technology evaluation that protects the org without putting innovation at risk.
(Source: https://www.zdnet.com/article/is-2016-the-year-of-it-disruption/ )
3 Questions IT leaders must ask when evaluating new tools
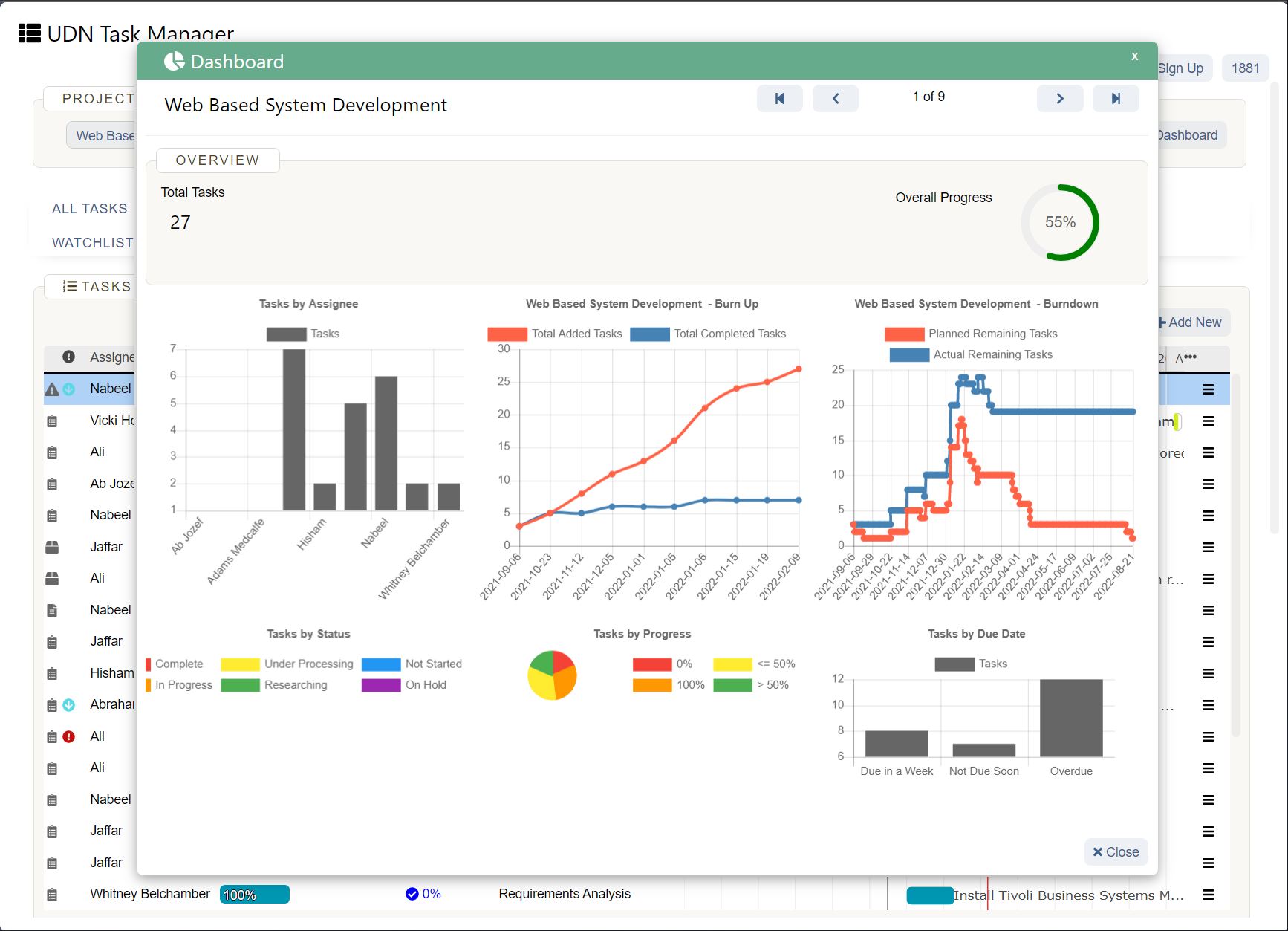
1. What is the purpose of the tool and how does it fit in the tech stack?
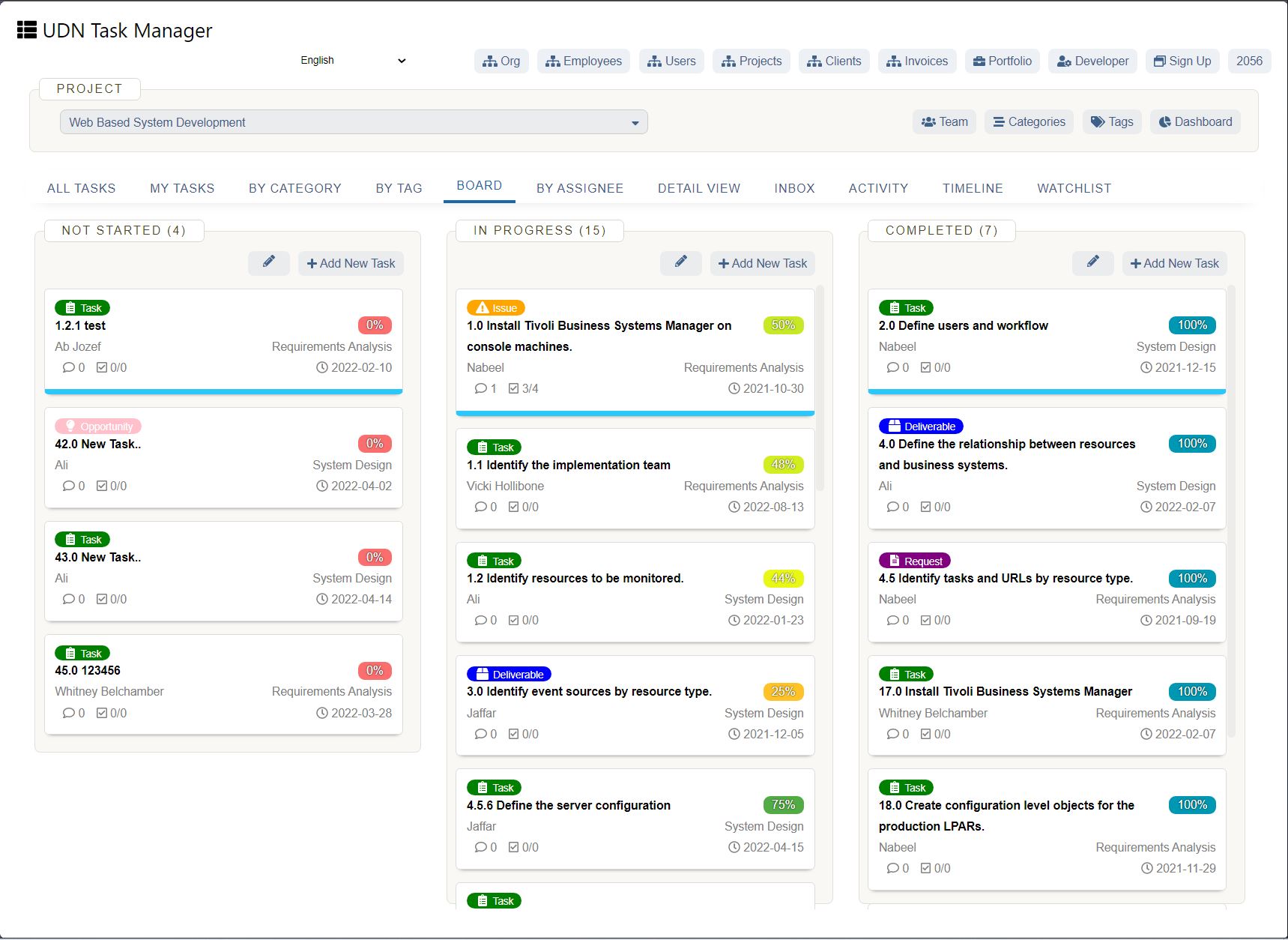
Every new piece of software or technology adds new complexity to existing systems and threats compound. More often than not, it’s better to reduce the number of moving parts when possible.
“I see it as the conga line of technology and security,” explains Szymanowski. “And with the conga line of technology, everything moves you away from your core functionality and the data that you protect. As more functionality is needed, you add new tools, devices, and processes to the chain. While it may be functional and necessary in the short term, it adds complexity that has the potential to become risks and weaknesses. For each one of the connections on the conga line, you need a structured approach to how you define requirements while overseeing and managing security for each of those parts. If two functions can be reduced to one, that's a better solution.”
When the focus becomes too centered on growth and execution, problems arise.
“The danger lies when thinking is overly shortsighted. “We’ll just do it (install it) because we need to get ‘X’ done.” You don't want to start adding onto that conga line. At some point, you're going to put something in there that violates law, negatively impacts data security, or worse, weakens previously robust systems.
2. Who made the tool and what is its reputation?
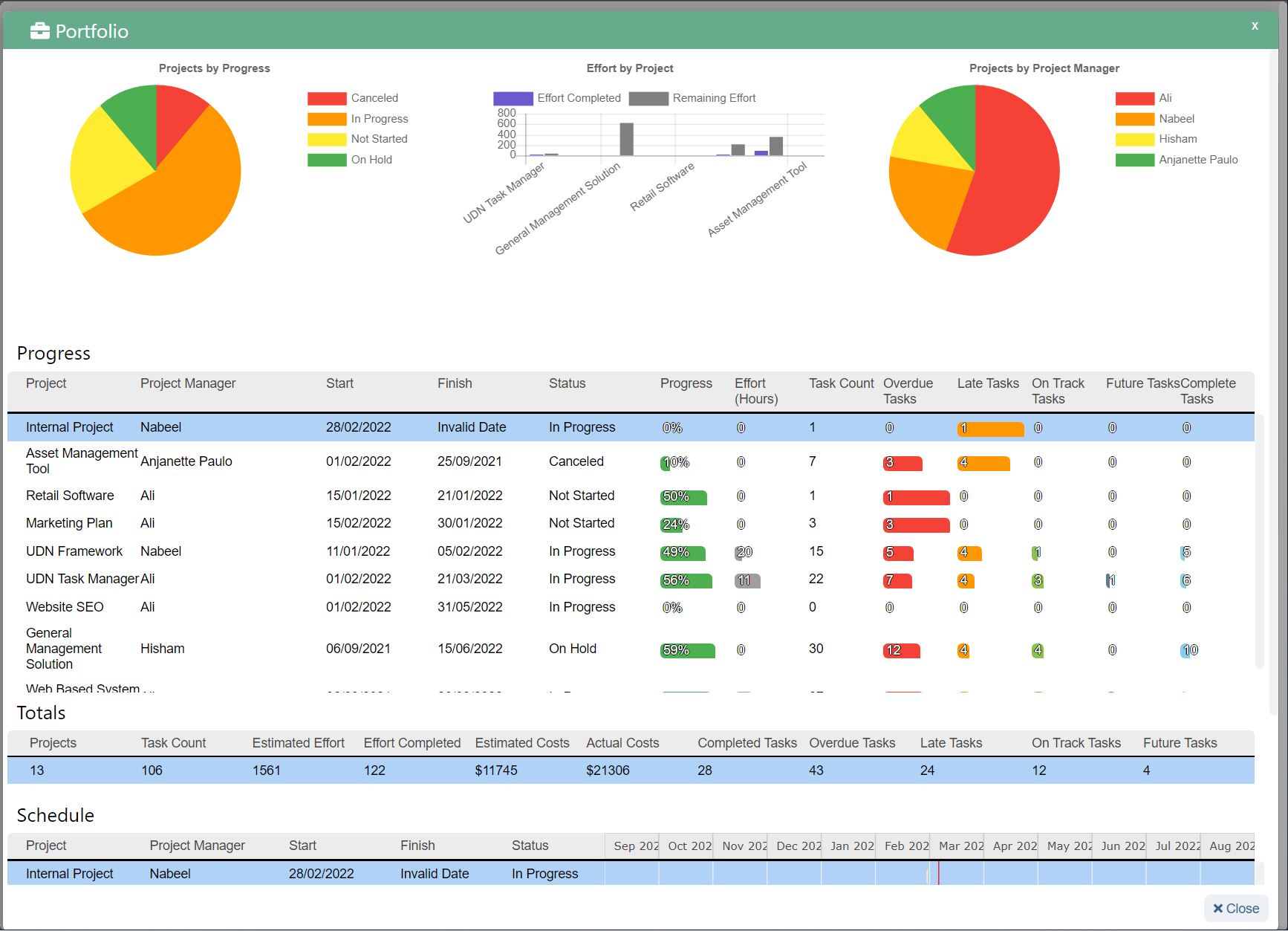
Where software comes from matters. An undersupported piece of software by a threadbare team that isn't well established can be a huge liability.
“You need to thoroughly evaluate any software partners,” shares Szymanowski.
“That cool piece of software from that small team you choose to use may be something you build critical infrastructure on. If that piece of software wasn't well thought out and designed, or the code behind that software isn't secure, it may detrimentally affect your business even when the technology concept is sound. A lot of great technology can come from small teams. Let's recall that HP was started by 2 guys in a garage! But what if a couple years down the road, the 2-person team that made your now critical software find themselves at an impasse and shut it all down? What if one of them decides to take all their data and IP and move on? That could have serious consequences.”
There may be pressure to adopt the latest tool or device as quickly as possible, but being too hasty can cause a myriad of problems down the road.
3. Do we have a plan to train users on data security best practices?
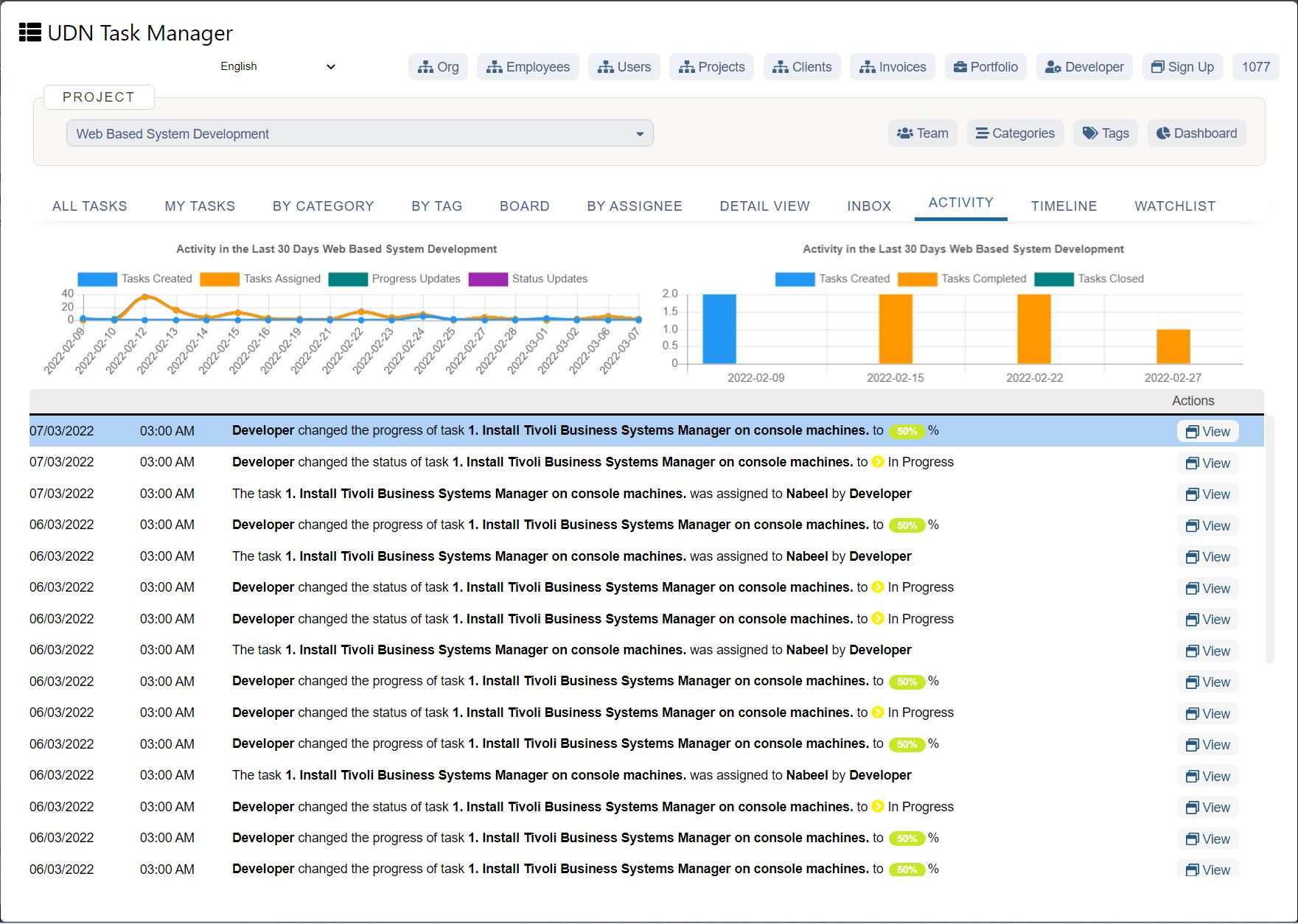
The vast majority of breaches and incidents are not the result of compromised technology — they’re the result of human error . IT leaders have to start viewing internal education as a critical part of their security infrastructure. Security policies and best practices must be made available. A culture of risk awareness, education, and responsibility has to be cultivated and built into an organization’s DNA.
“The cloud has been the biggest change,” explains CIO advisor and security consultant Dustin Bolander . “Dropbox, Google Apps, etc. have made it incredibly easy for documents to escape the organization. Now any user in the company can set up a service and be storing data in the cloud in a matter of minutes. This has resulted in a big change from relying on technical safeguards to having to focus on user awareness and security training.”
Given the pace at which technology advances and evolves, providing basic data handling best practices and security training may be the best step an org can take to prevent a costly breach. Our founder and CEO, Andrew Filev, outlined some great data privacy practices here .
Security Is the New Differentiator
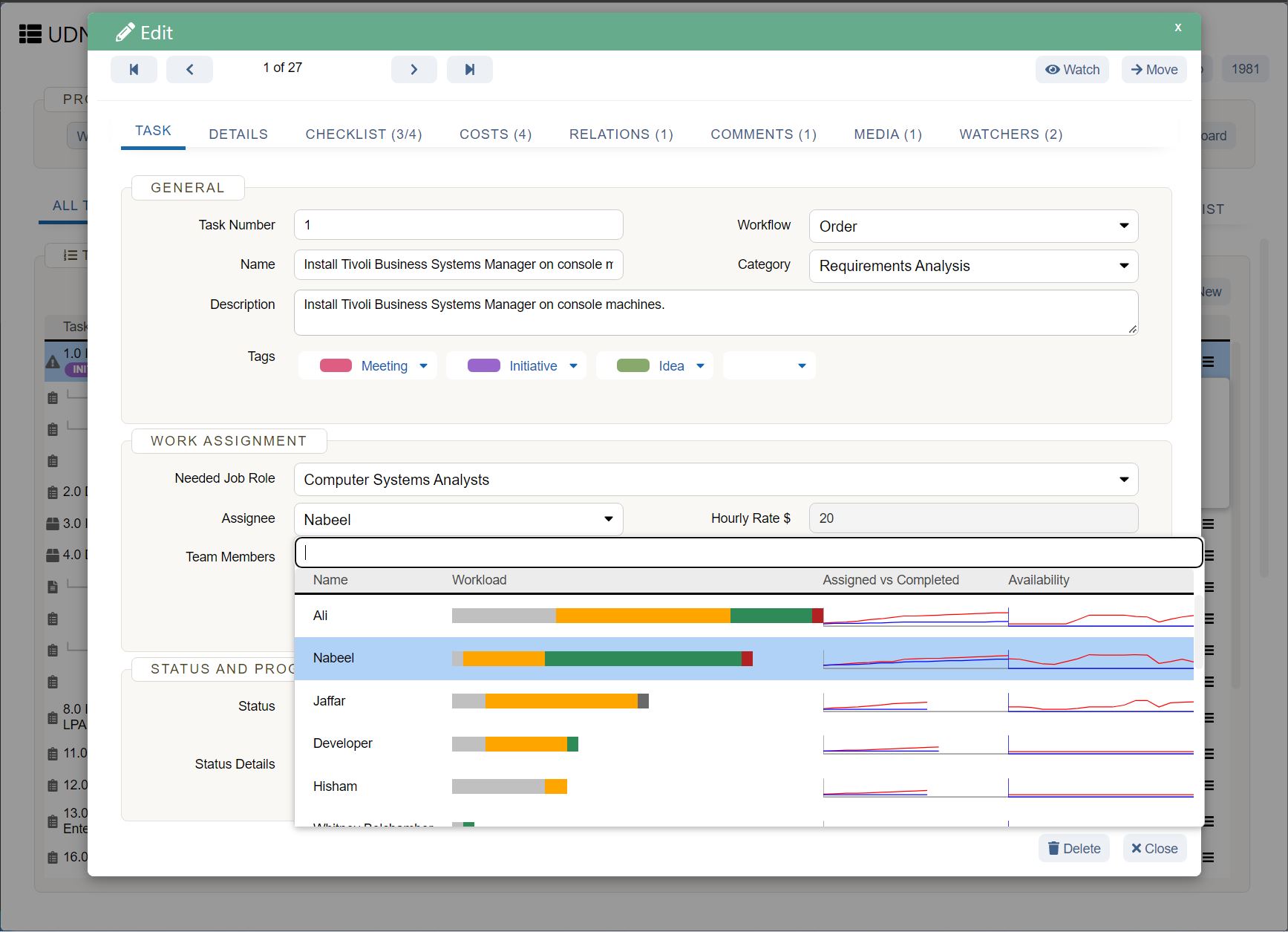
Companies need to make security a bigger priority than ever before and review it considerably earlier in the vendor vetting process. Data breaches will always be a threat, but a serious danger lies in restricting the ability of teams to be innovative. Organizations need to find responsible ways to enable openness and creativity without compromising security.
Customers expect their data to be safe. It’s been estimated that the mishandling of data and security will cost Facebook alone over $1 billion . Every piece in your tech stack has the ability to compromise data and damage your organization, so hold them to a high standard.
At UDN Task Manager we haven’t just kept us with security standards, we’ve pioneered them . Our commitment to security is not just bragging about new bells or whistles. We’re dedicated to keeping our customer’s data safe because we know their businesses depend on us. And with new features like UDN Task Manager Lock , our users now have unparalleled control over their data in the cloud.
All of these security features serve one purpose: to enable seamless collaboration. Distributed teams can collaboratively manage their work with ease, knowing their data is protected by industry-leading cloud security. Are you ready to empower your team to innovate across distances? Start your free trial today.
Photo by sebastiaan stam on Unsplash











