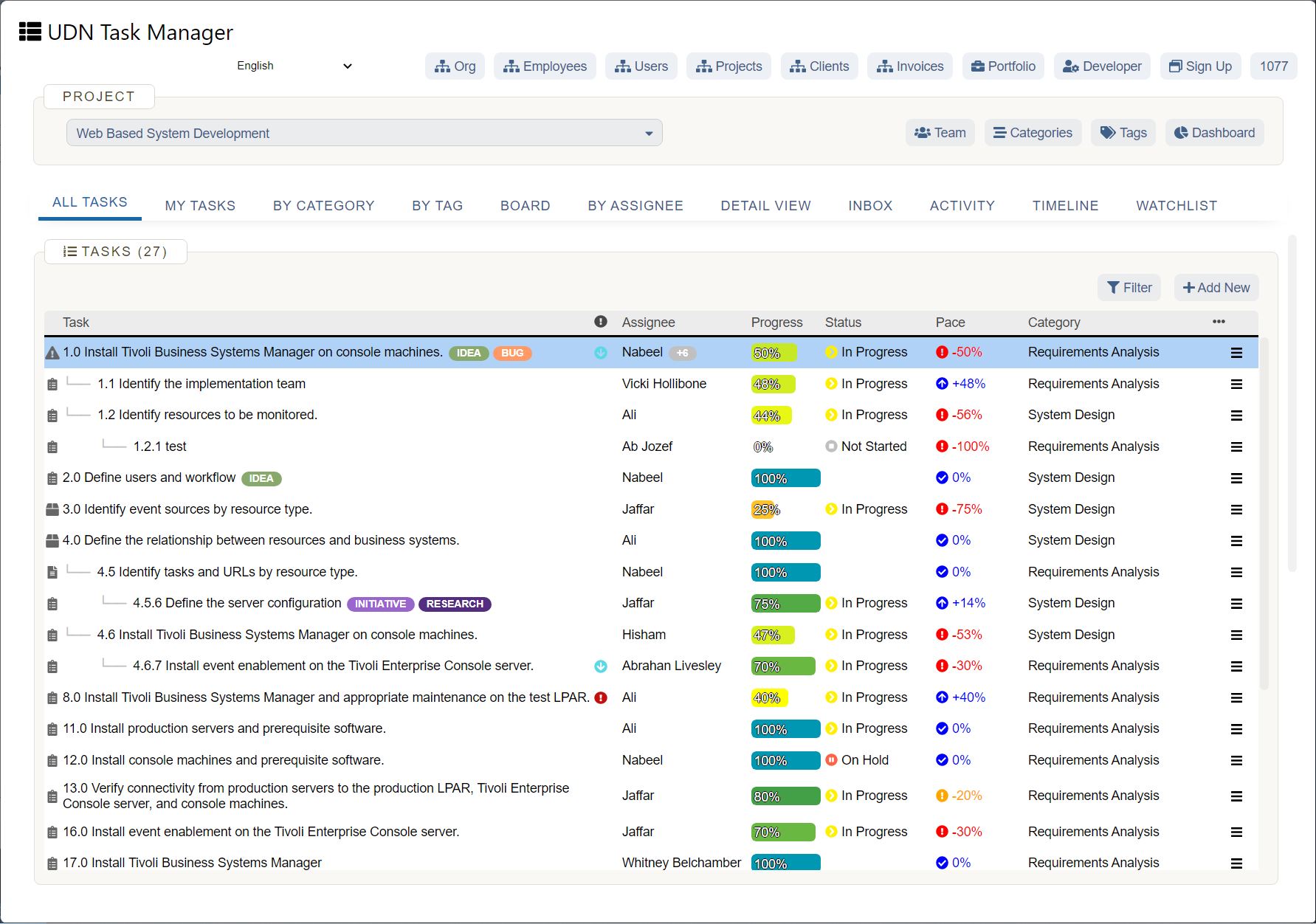
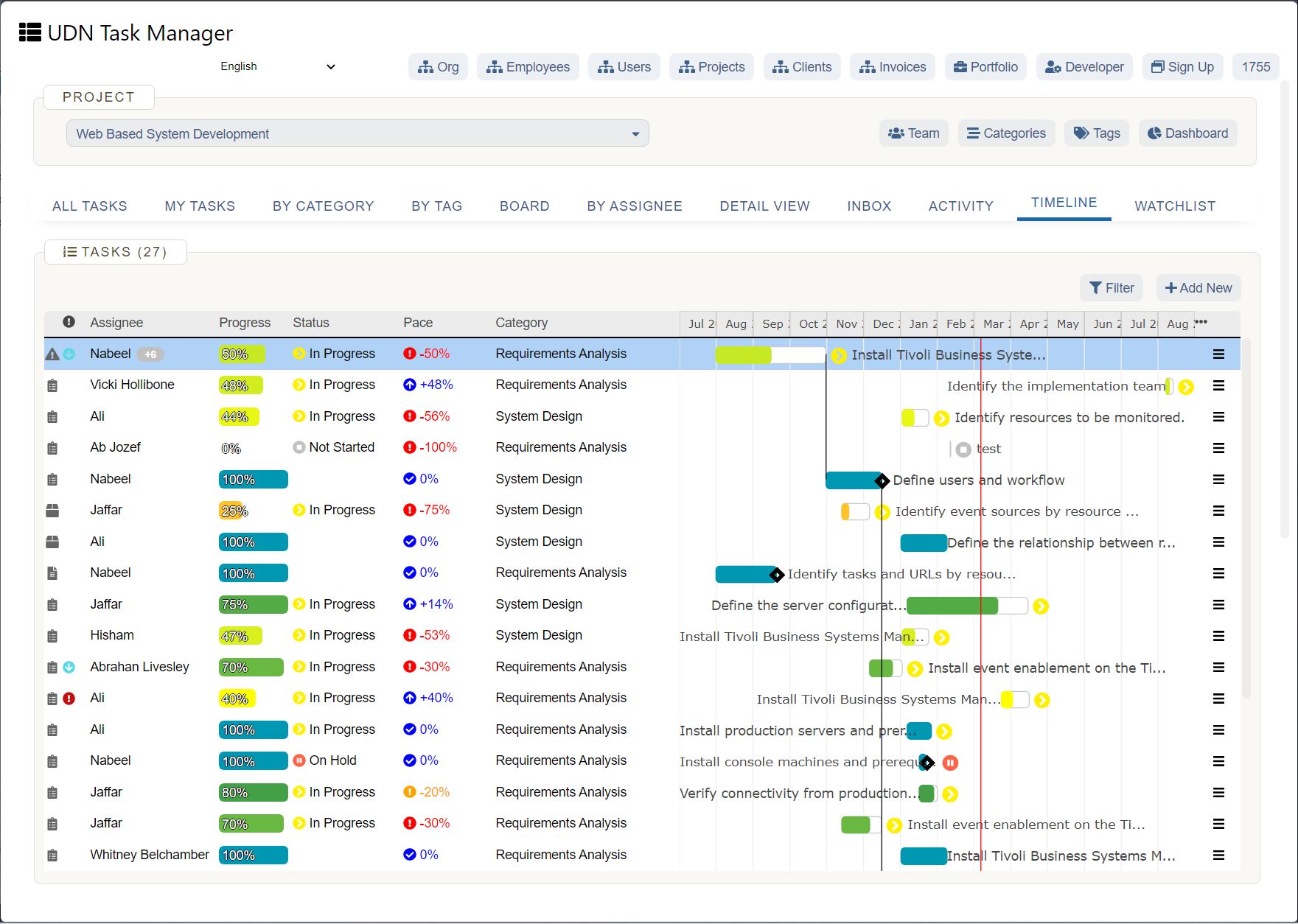
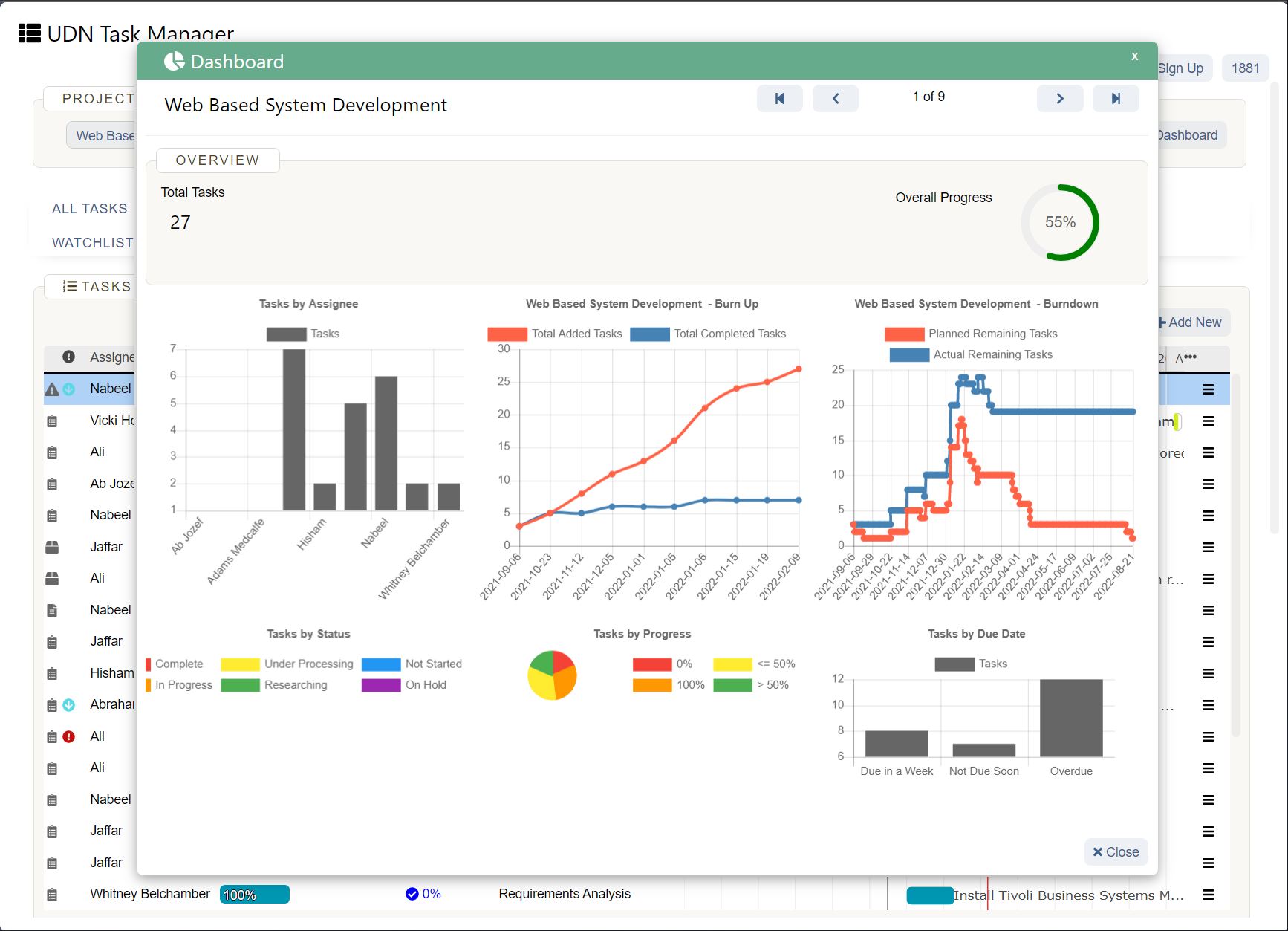
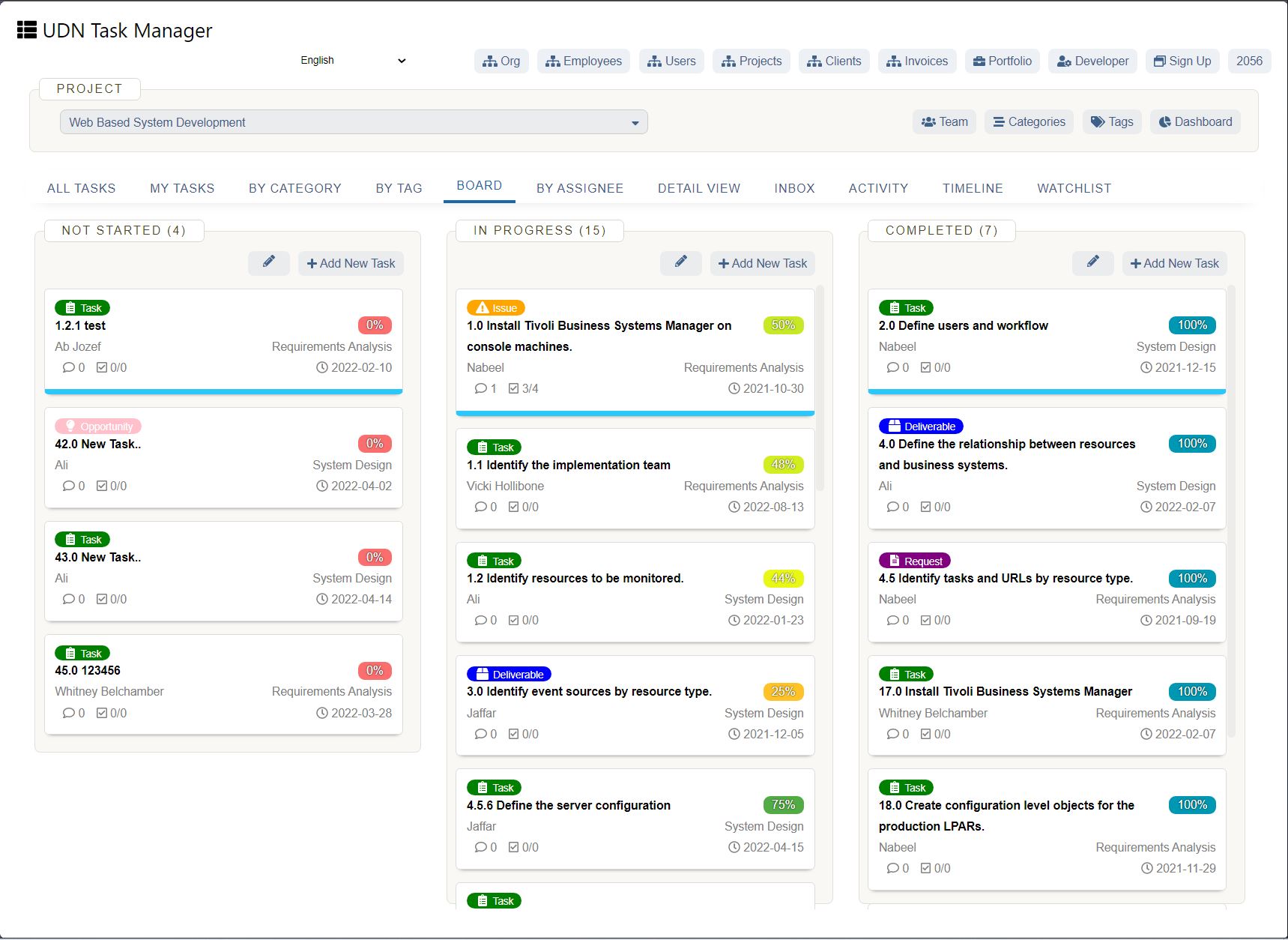
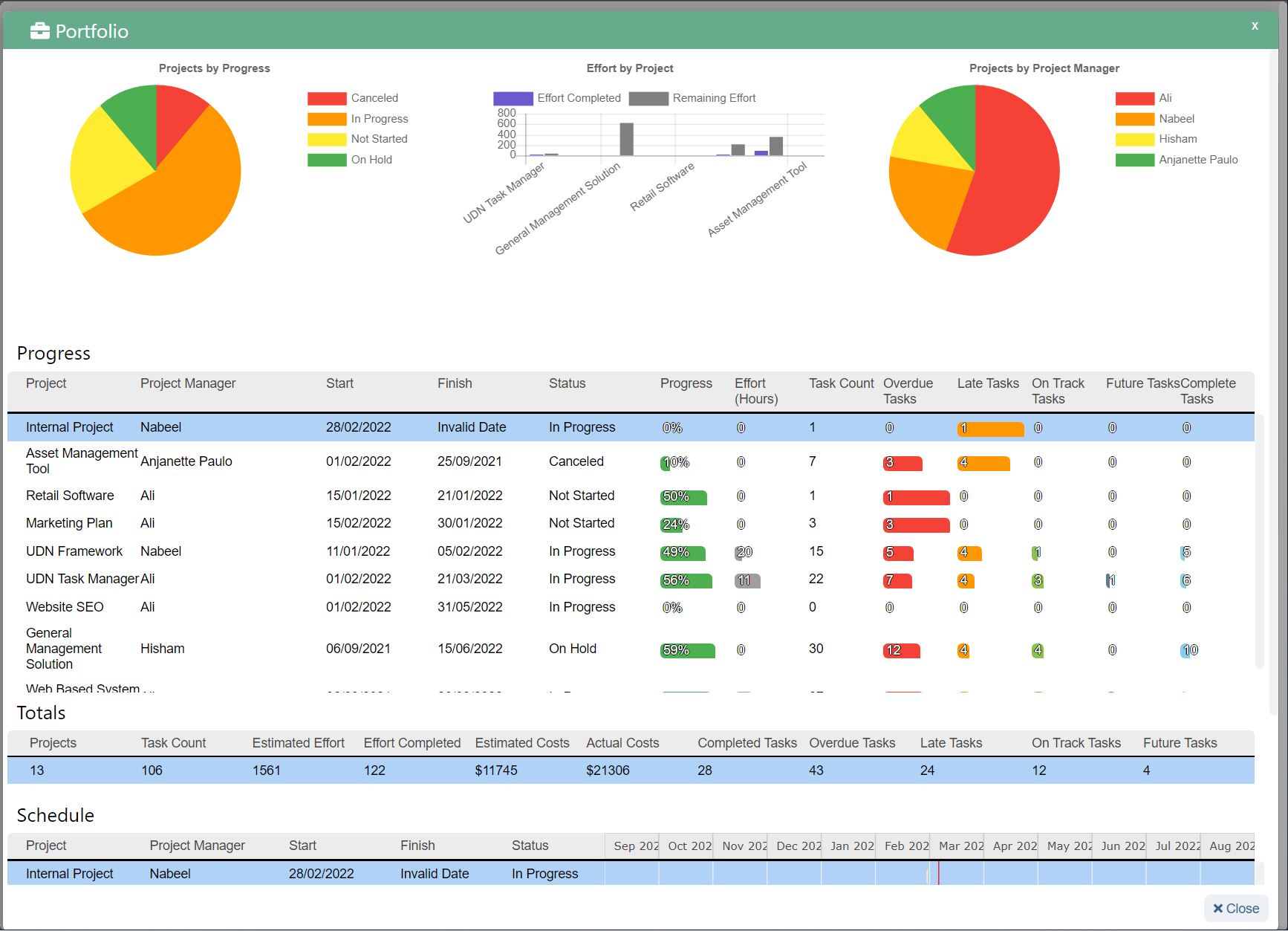
Your Collaborative Work Management Security Checklist
2018 will go down in history as the year some of the world’s most notable companies experienced huge data breaches . Even social networking tech giant Facebook made countless headlines as it dealt with a slew of major security attacks that affected more than 100 million users .
The average data security incident cost U.S. firms $7.91 million , and there’s something priceless at stake — customer trust. With the first breach of 2019 occurring less than 24 hours into the new year, this threat isn’t going away, and security should be a top concern when considering new tools for your tech stack.
One tool you need to take another security look at? Your work management platform. Sure, you could keep your work in Excel or try to hide from the cloud, but over 250,000 organizations have adopted a work management solution, and you need one to stay competitive . These tools improve collaboration, increase productivity, enhance visibility, and — if you get the right one — provide security . All of these are critical for business growth.
Here's a checklist of the major security requirements to help you evaluate which collaborative work management solution is right for you:
Your work management security checklist defined
Security where your data is physically stored
Is the work management tool provided by a global business? Where do they physically hold their data? Different states and countries have very specific data-security compliances laws. One state’s security laws might not align with your needs. Ask where the company stores its data, and make sure the security standards at the storage facility are up to date.
For example, our data center in the U.S. is compliant with SSAE 16 Type II and ISO 27001 standards, and our European data center is compliant with ISO 27001 and ISAE 3402 standards (equivalent to SSAE 16). All server and network components are constantly monitored by UDN Task Manager staff and our colocation providers.
A creepy, masked cyber hacker staring at multiple screens while typing vigorously (like on TV) isn’t your only threat. Ask about the physical protection of the storage facilities like 24/7 manned security, power backup systems, physical access controls, smoke and fire alarms, and digital surveillance systems.
Disaster recovery plans and certifications
Is the vendor’s plan in case of a disaster scalable and secure? UDN Task Manager 's disaster recovery infrastructure resides in Google Cloud Platform for both U.S. and E.U. regions, offering great scalability and security with SSAE16 / ISAE 3402 Type II, ISO 27001.
An ISO 27001 certification means that the vendor has implemented industry best practices in security-incident management and physical security. It shows that the vendor has systemized controls to limit any damage to your organization in the case of an attack. This increased security reliability means you can be confident in sharing sensitive data.
You also want to make sure that data is both backed up and available on redundant and geographically dispersed servers. Ask how frequently a full backup is performed and if it’s stored in an encrypted environment that is physically separated from the primary servers.
Continuous reliability
Uptime is a computer industry term for the time during which a computer is operational, meaning that no malfunction occurred. A tool is only useful if it can be used. High uptime means a company is stable, secure, and experienced. Ask what the vendor’s uptime is to determine their security reliability.
As an example, over years of continuous service, UDN Task Manager has consistently met or exceeded a 99.9% uptime, ensuring customers can access their tasks and projects when needed without interruption.
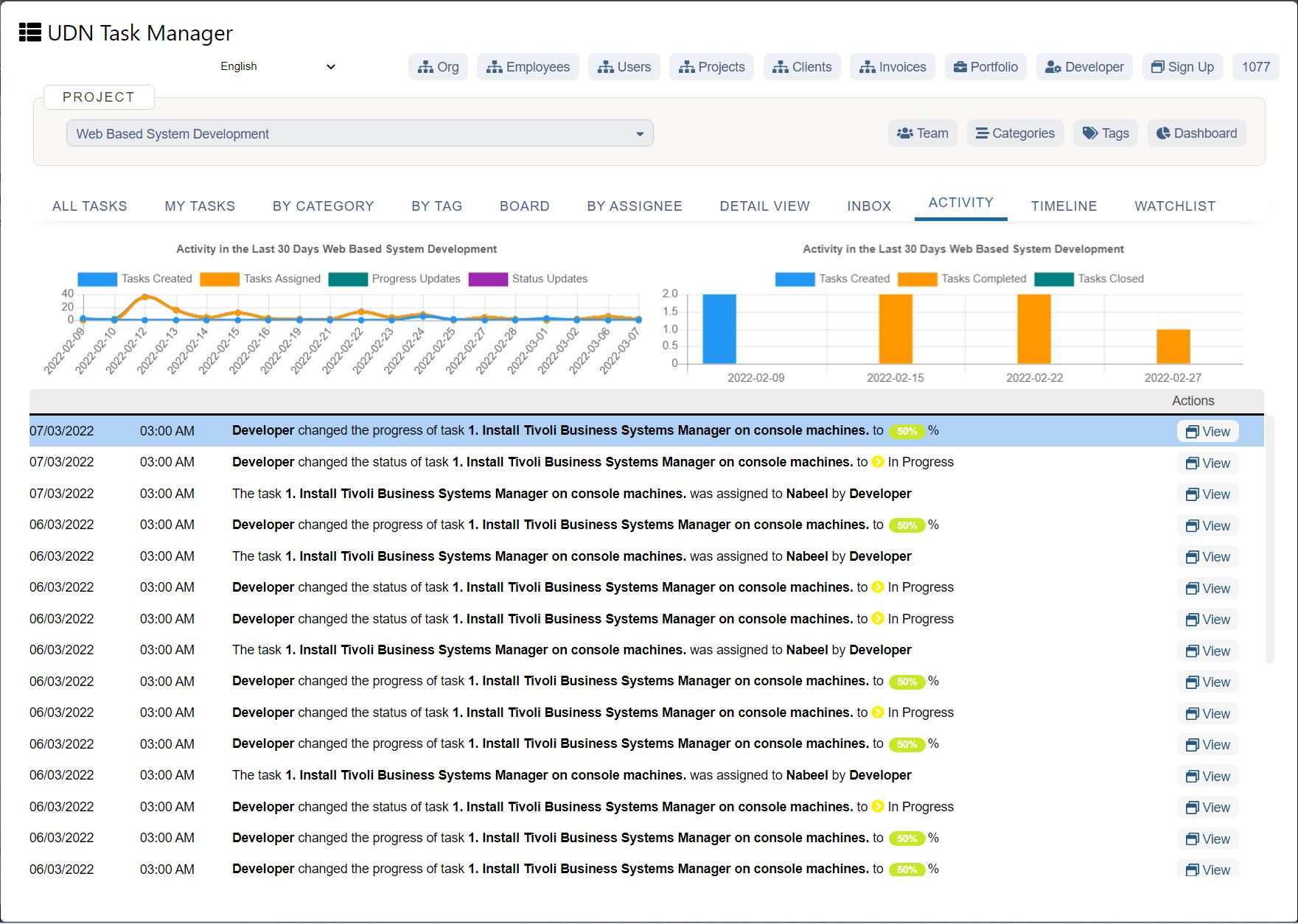
Network and system security
What procedures are used to prevent, detect, and promptly remediate the impact of malicious traffic and network attacks? Do you have a contingency plan if these attacks happen? Are there regular updates and patch management? Understand how frequently the vendor performs internal network security audits so they can easily spot and fix dangers. When it comes to data security, a quick response is the key between danger and disaster.
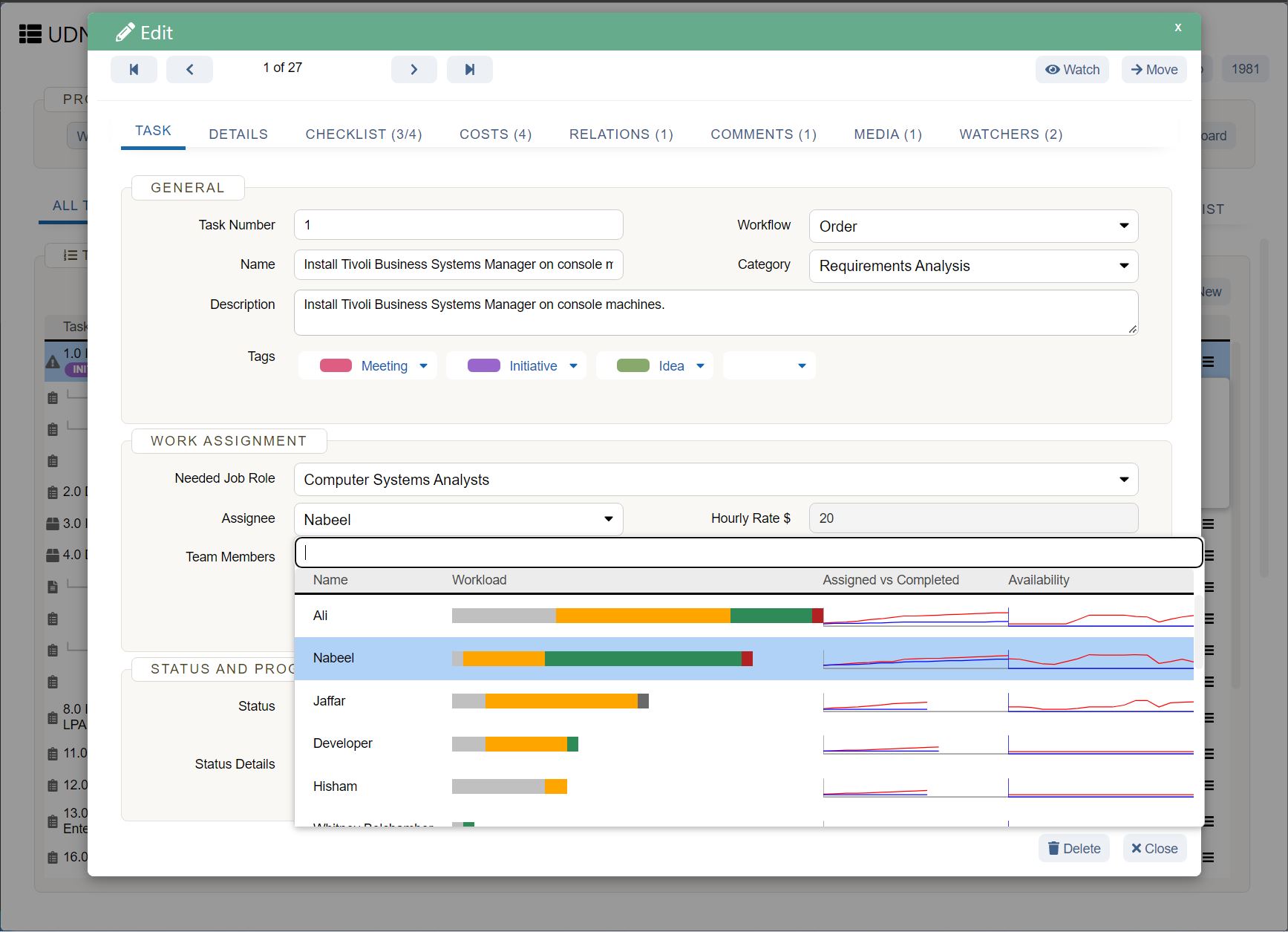
User authentication programs
What are the protection and password policies? Even if your team is well trained and using passwords more powerful than “Password123,” email and password combinations are a huge hacking danger . Look for tools that will help your employees secure their data. For example, UDN Task Manager supports multiple methods of federated authentication, including Google Open ID, Azure, Office 365, ADFS, SSO, and SAML2 to conveniently and securely gain access to a UDN Task Manager account leveraging corporate credentials.
Bonus! Is the vendor’s platform available on mobile? It's essential that user authentication programs serve an increasingly dispersed workforce, and can be compatible with remote working software . Understand which security functionalities are inherited and what additional security features are provided, like certificate pinning, checking against rooted/jailbroken devices, and application-level protections using a PIN code or fingerprint.
Customer support policies
Ripping your hair out over login and platform issues is a huge security risk . Your hair could fall on the ground and that DNA can be used to log in. Joking!
However, you want to make sure the vendor has strict policies on how to verify your identity and help you access your account. Knowing how their team can access your data if needed helps you keep it secure. They should have policies that allow you to dictate when and how they see your data. Ask vendors to share their policies around escalation, management, knowledge sharing, risk management , and day-to-day operations.
Who in the vendor's organization has access to the data center? There should be strict policies in place. For example, at UDN Task Manager , access requires establishing a VPN channel, multi-factor authentication, a one-time password, and a personal certificate. As a best practice, we also have policies in place to limit access to customer data to employees with a job-related need. When teams are trained and have strict policies, you dramatically reduce data security risk.
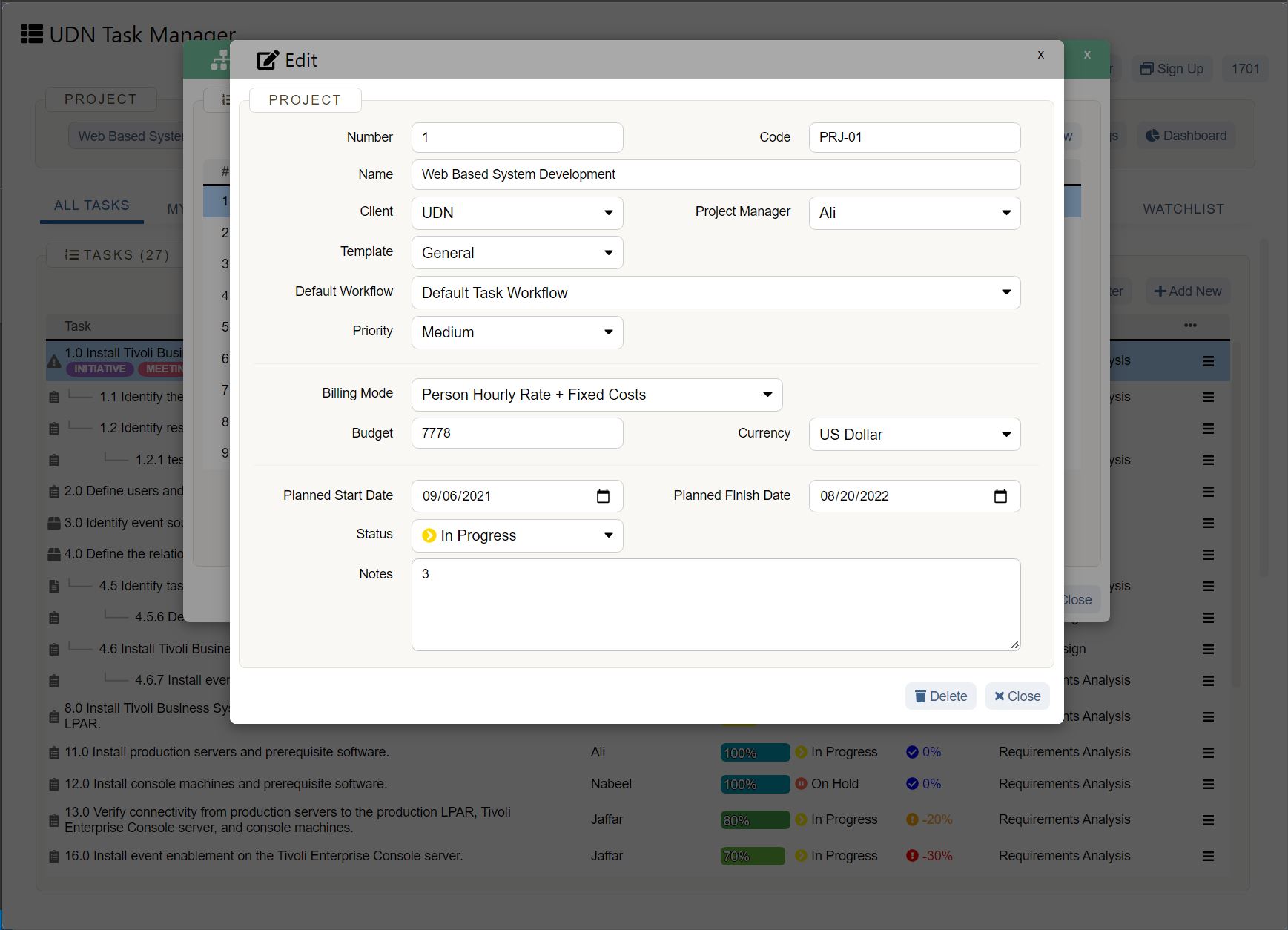
Data privacy and encryption

What type of data security certifications and compliances does the vendor have? Do they align with your business requirements? What third party is doing their security assessments?
Understanding what technology is protecting your information helps you ensure that your data is secure beyond measure. Even if someone was able to gain access to your data, they can’t read it directly if it’s encrypted. Thus, an extra layer of much-needed protection.
Stay nimble and secure with UDN Task Manager
In our recent study of 1,000+ professional services leaders, 75% said that data security was a big concern for clients, and 60% reported that those concerns kept them from being agile or building strong relationships.
It may not sound intuitive, but security is at the heart of collaboration . Whether your business is B2B or B2C, teams need a safe space to communicate, innovate, and work, so they can stay on top of projects and maximize creativity.
As you review vendors for work management platforms, consider that cost and make security a top priority. A tech stack that prioritizes security does more than just save you money by avoiding costly breaches. When your team has a safe space to get creative, innovate, and collaborate, you differentiate yourself from the competition and empower your business to stay at the forefront of your industry.
Along with being the leading collaborative work management platform, UDN Task Manager continues to be a pioneer in security . We‘re dedicated to making UDN Task Manager the most secure and reliable collaborative work management platform on the market. We’re always adding new tools and features to help teams stay nimble but secure. UDN Task Manager Lock , for example, lets you own and manage the keys to your encrypted UDN Task Manager data, giving you increased control even over data in the cloud.
Our advanced security features help your teams focus on what really matters. Want to learn more about how UDN Task Manager helps you stay secure as you grow your business? Start your free trial today .











